- Uninstall Forescout Secure Connector Mac
- Forescout Secure Connector Download
- Forescout Support
- Forescout Secure Connector Mac Mini
What is Forescout CounterACT?
ForeScout CounterACT® is an agentless security appliance that dynamically identifies and evaluates network endpoints and applications the instant they connect to your network.
The Forescout platform provides your security operations and incident response teams with a consolidated, real-time view of your device landscape along with classification, connection and compliance context. The Forescout Device Intelligence Dashboard is easily customizable for other IT functions such as risk, compliance and executive reporting.
Get the most out of your Forescout license or product. Installation guides are available in multiple languages. Click below to download. Forescout 8.2 Quick Installation Guide Forescout 8.1 Quick Installation Guide Forescout CounterACT 8.0 Quick Installation Guide Forescout CounterACT 7.0 Quick Installation Guide Visit Customer Support Portal for additional support. Access Product Software. Forescout’s flagship product, ForeScout 8.2—a unified device visibility and control platform for IT and OT networks, dynamically identifies and evaluates network devices and applications as they connect to an organization’s network. Allows SecureConnector to create a secure (encrypted TLS) connection to the Appliance from OS X machines. SecureConnector is an agent that enables management of OS X endpoints while they are connected to the network. Refer to the Forescout Administration G uide for more information about SecureConnector. Ternyata untuk uninstall ForeScout Secure Connector bisa membuat gemes, karena jika ForeScout ini sudah disetting sebelumnya oleh Network Administrator dengan menanamkan password ke dalam installer ForeScout yang diberikan kepada kita, dan suatu saat ketika tidak butuh lagi adanya ForeScout di Laptop/PC dan ingin meng-uninstall aplikasi ini pasti akan diminta untuk memasukkan password, padahal.
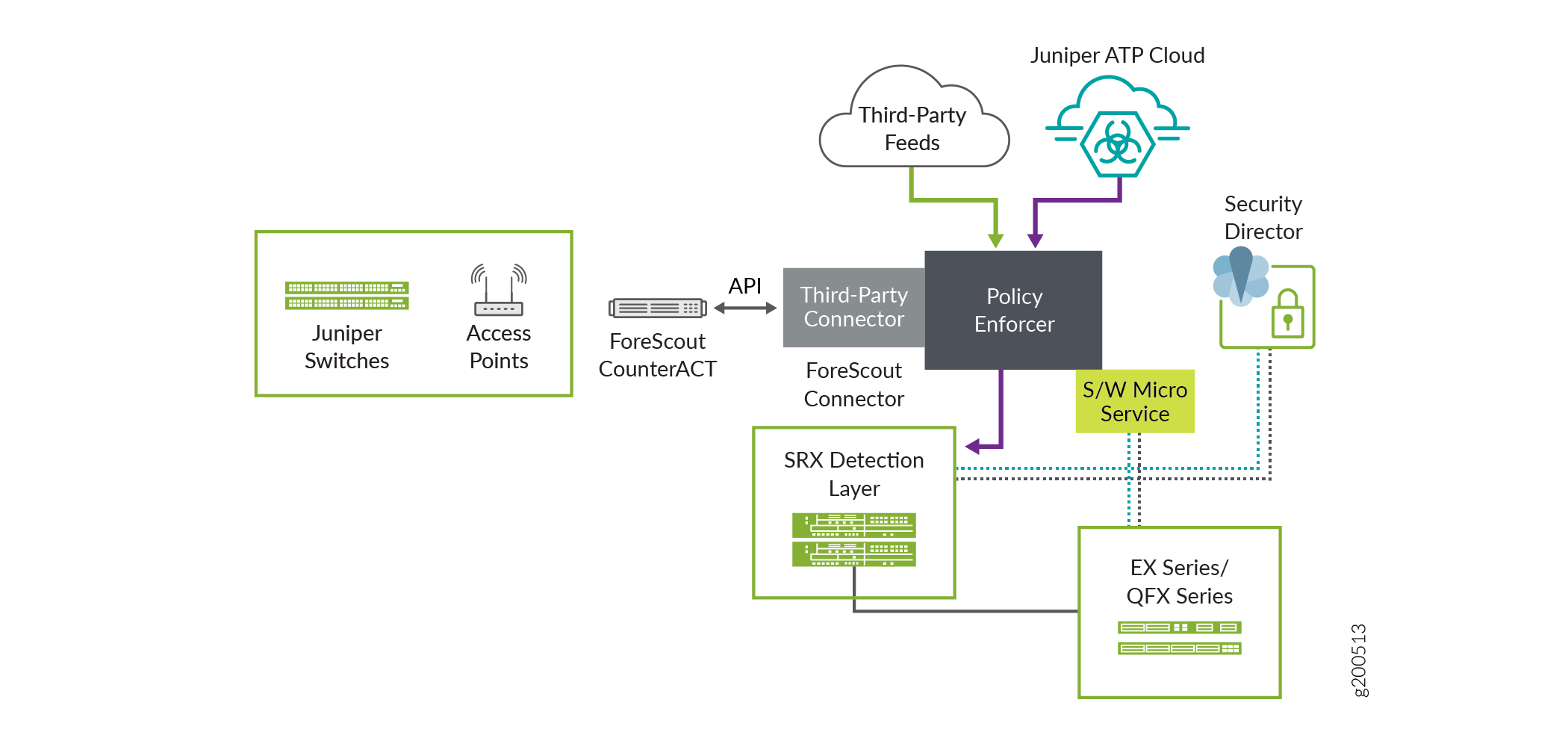
How does Forescout CounterACT work?
CounterACT discovers and classifies devices without requiring agents. Based on its classification, CounterACT then assesses the device’s security posture and applies policies that enforce the specific behavior the device is allowed to have while connected to a network. See More.
What is a NAC solution?
Network Access Control (NAC) is a computer networking solution that uses a set of protocols to define and implement a policy that describes how to secure access to network nodes by devices when they initially attempt to access the network.
What is the best NAC solution?
Top NAC solutions
- Extreme Networks ExtremeControl.
- Auconet BICS.
- ForeScout CounterACT.
- Pulse Policy Secure.
- HPE Aruba ClearPass.
- FortiNAC.
- Cisco Identity Services Engine.
- InfoExpress CyberGatekeeper.
Why do we need a NAC solution?
NAC systems can play a vital role in automatically identifying devices as they connect to the network and providing access that does not potentially compromise security. For example, when a personal mobile device connects, it can be granted access only to the Internet and not to any corporate resources.
What are the three key activities performed by NAC nse2?
What are the three key activities performed by NAC? (Choose three.) Discover all devices on the network. Profile all devices to identify what access they should have. Provide appropriate network access to devices.
What is extreme NAC assessment agent?
Extreme Networks NAC provides agent-based or agent-less endpoint assessment capabilities to determine the security posture of connecting devices.
Can ExtremeControl provide visibility and control on non extreme network devices?
ExtremeControl unifies the security of wired and wireless networks, providing visibility and control over users, devices and applications. It enables granular policy controls to help users comply with policies and compliance obligations in heterogeneous endpoint environments.
What is port-based access control?
Port-based network access control regulates access to the network, guarding against transmission and reception by unidentified or unauthorized parties, and consequent network disruption, theft of service, or data loss. Data frames are transmitted and received using the MAC Service specified in IEEE Std 802.1AC.
What is Cisco NAC?
Cisco Network Admission Control (NAC) is a set of technologies and solutions that uses the infrastructure of a computer network for network access control (NAC) and network protection. All access methods are monitored, including wireless devices, local area networks (LAN) and remote access wide area networks (WAN).
How do I give someone access to my network?
Network Administration: Granting Share Permissions
- Open Windows Explorer by pressing the Windows key and clicking Computer; then browse to the folder whose permissions you want to manage.
- Right-click the folder you want to manage and then choose Properties from the contextual menu.
- Click the Sharing tab; then click Advanced Sharing.
- Click Permissions.
What is Cisco NAC agent used for?
The Cisco NAC Web Agent provides temporal posture assessment for client machines. Users launch the Cisco NAC Web Agent executable, which installs the Web Agent files in a temporary directory on the client machine via ActiveX control or Java applet.
What is CCAAgent?
The application listens for or sends data on open ports to a LAN or the Internet. CCAAgent.exe is able to monitor applications.
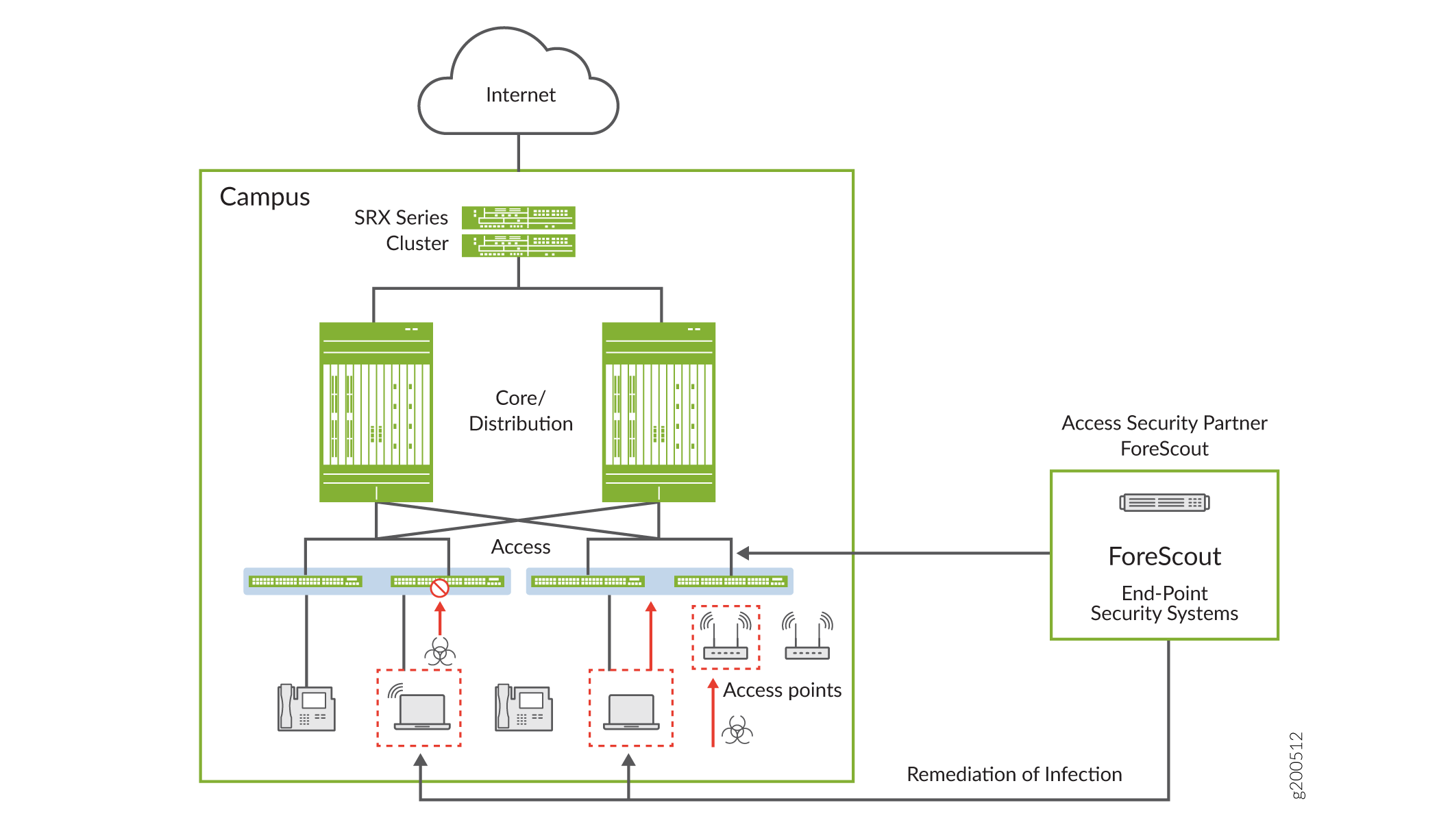
Is Cisco ISE an appliance?
Cisco ISE comes preinstalled on a range of physical appliances with various performance characteristics. The Cisco Application Deployment Engine (ADE) and Cisco ISE software run on either a dedicated Cisco ISE 3300 Series appliance or on a VMware server (Cisco ISE VM).
Uninstall Forescout Secure Connector Mac
Is Eapol secure?
Digital certificates are an essential part of 802.1x authentication. Certificates are shared, checked, and verified before any device is allowed to connect to the network. A secure channel is used during the negotiations, so all credentials are safe from prying eyes.
What is port security on a switch?
Port security is a layer two traffic control feature on Cisco Catalyst switches. It enables an administrator configure individual switch ports to allow only a specified number of source MAC addresses ingressing the port.
Which subcommand overrides the default action to take upon a security violation?
4. (Optional) Use the switchport port-security violation {protect | restrict | shutdown} interface subcommand to override the default action to take upon a security violation (shutdown).
What is the default port security violation mode?
Switchport Violations These are described in more detail below: Shutdown – When a violation occurs in this mode, the switchport will be taken out of service and placed in the err-disabled state. The switchport will remain in this state until manually removed; this is the default switchport security violation mode.
How do I check my port security violations?
Here is a useful command to check your port security configuration. Use show port-security interface to see the port security details per interface. You can see the violation mode is shutdown and that the last violation was caused by MAC address 0090.
Which action will bring an error disabled switch port back to an operational state?
Which action will bring an error-disabled switch port back to an operational state? Clear the MAC address table on the switch. Remove and reconfigure port security on the interface. Issue the switchport mode access command on the interface.
Removal guide for software 'secureconnector.exe' on Windows (XP, Vista, Win7, Win8 and Windows 10) systems. Tips for getting it away from the hard disk
How to permanently delete secureconnector.exe from your computer:
First, please read this important warning: This article shows a general guide how to remove any file from your computer. It DOES NOT implies that secureconnector.exe is harmful! Be aware of removing executable files from your computer without deeper knowledge of what you're doing. First of all, because of secureconnector.exe is an executable, there is always a possibility that removing this file MAY damage the operating system or even your data.
Are you still ready to remove secureconnector.exe? OK, let's go for it. Here is the guide:
- Create Restore point for Windows (not available in Windows XP). Restore point will help you to revert changes, if something'll go wrong.
- Press F3 key to open standard search window. Than type 'secureconnector.exe' into search box. In couple of minutes, seconds if you're lucky, Windows will find all the copies.
- Try to locate program, to which the process secureconnector.exe belongs. Than try to uninstall that program in a standard way.
For example, if secureconnector.exe is found in folder C:Program FilesDummy game**some subfolder**, it most probably belongs to 'Dummy game' software package. - If your problem persist and you are not able to remove file that way, go to the search results (step 2) and try to manually delete all the occurrences of secureconnector.exe.
Note: If the process is running, you will not be able to delete the file. In such situation, you must stop the process via Task manager (right click on Windows task bar, select 'Task manager'. In Task Manager windows, click 'Processes' pane. Than select secureconnector.exe and press 'Delete' key). Detailed guide. - Some malware can hide itself under different names (so-called 'clones'). To remove such self-hiding program, use specialized tool 'EasyRemove' - see below
EasyRemove is lightweight and easy-to-use removal tool for secureconnector.exe
Download EasyRemove and get your computer fixed within minutes.
You can be also interested in: checking if secureconnector.exe is virus or not , how to solve typical problems with secureconnector.exe error (or more specific secureconnector.exe application error) Solve problems with secureconnector.exe not responding. Typical Windows message: secureconnector.exe high cpu. How to handle damaged file: secureconnector.exe is corrupted.
Main article: secureconnector.exe
You know it: the longer you own your computer, the slower it runs and the more often it stucks.
EUROBYTE TOOLS speeds up more than 1 million computers around the world. Try it now:
Forescout Secure Connector Download
Security risk rating: N/A
Note: The security risk rating is based on user's opinions. This is not our recommendation or adwice any way. Please use your own mind and think twice :-)
Trojan and malware info: N/A
Typical errors: File not found, An error occured in file, Not responding, Application Error 0x , Howto delete, stop, run, remove and find the file...
Notes:
- N/A is an abbreviation for 'Not available'. That means that now we have no information if this process is harmful or not.
- There is almost unlimited numbers of messages that should appear while you're running the software. We selected only the typical ones here
Related posts for secureconnector.exe
See Related Forum Messages: Follow the Links Below to View Complete Thread
Summary: 0 user rated this process.
Nameparts: se cureconnector, sec ureconnector, secu reconnector, secur econnector, secure connector, securec onnector, secureco nnector, securecon nector, secureconn ector, secureconne ctor, secureconnec tor, secureconnect or, .User reviews snapshot:
[22:24:06] kms-qad.exe: malware analiz...
[00:22:19] sandisksecureaccessv2_win.exe: how to restore the flasdisk sa...
[20:58:22] dx8vb.dll: the risk is virus ...
[14:18:21] nvspcaps.exe: NVIDIA Server Capture is neces...
[20:01:40] pcacli.dll: If you have a game or anything...
[22:42:35] half_life_2_lost_coast_gdf.dll: halmacpi.dll...
[06:33:34] nvgftraypluginr.dll: NvGFT Plugin.dll ...
[20:21:06] ivms-4200.exe: Process required for IVMS CCTV...
[19:16:19] pclink.exe: Wireless Printing software for...
[00:18:37] mcnetwork.dll: amze...
Warning: Once again about user reviews. Our users can freely add their reviews about whatever process they want. We, of course, purify and filter raged words. However, do not trust everything. We have no time to review any user's sentence. So the information provided in user reviews CAN be innacurate. Or misprinted. Or anything else. Are you adult, aren't you? We believe in your mind.
Forescout Support
Windows process DB: sptd.syscfp.exentkrnlpa.exehidfind.execonsent.exeswitchboard.exewerfault.exetrustedinstaller.exegrpconv.exefunshioninstall.exebservice.exedriver.exedf.execonhost.execli.execfpupdat.execcsvchst.exeavp.exeavastsvc.exeatiedxx.execcsrvc.exeshellker.exeiemonitor.exehardcopy pro.exehpzstc09.exehpzstw09.exestray.exemzccntrl.exetodslmgr.exetodslsvc.exe
New: Windows dynamic link library DB: csamsp.dll, ver. 5.1.2600.0 (xpclient.010817-1148), csaolinst.dll, ver. , CSAPI3T1.DLL, ver. 1.0.2216, csapi3t1.dll, csbiinst.dll, cscdll.dll, cscdll.dll, cscomp.dll, CSCSaFX.dll, cscsvc.dll, cscui.dll, cscui.dll, cscui.dll, Csh.dll, csh.dll, dllhost etc...
Available version list table, select the version you have on your PC:
Forescout Secure Connector Mac Mini
| Security | MD5 or checksum | Version | Location | Size |
Retypes: wxe, rxe, eze, ece, exw, exr, eexe, exxe, exee, aecureconnector, decureconnector, swcureconnector, srcureconnector, sexureconnector, sevureconnector, secyreconnector, secireconnector, secueeconnector, secuteconnector, securwconnector, securrconnector, securexonnector, securevonnector, securecinnector, securecpnnector, securecobnector, securecomnector, secureconbector, secureconmector, secureconnwctor, secureconnrctor, secureconnextor, secureconnevtor, secureconnecror, secureconnecyor, secureconnectir, secureconnectpr, secureconnectoe, secureconnectot, ssecureconnector, seecureconnector, seccureconnector, secuureconnector, securreconnector, secureeconnector, securecconnector, securecoonnector, secureconnnector, secureconnnector, secureconneector, secureconnecctor, secureconnecttor, secureconnectoor, secureconnectorr, ecureconnector, scureconnector, seureconnector, secreconnector, secueconnector, securconnector, secureonnector, securecnnector, secureconector, secureconector, secureconnctor, secureconnetor, secureconnecor, secureconnectr, secureconnecto, zecureconnector, secureconnecdor,
Disclaimer
This web site and all information written here is for information purposes only, WITHOUT ANY VARANTY. YOU ARE USING THIS PAGES ON YOU OWN RISK. You should always verify the accuracy of information provided on this page. We pay a big attention to provide you with the correct information. However, many spyware and malware programs use filenames of usual, non-malware processes and DLLs. If we have included information about secureconnector.exe that is inaccurate, we would appreciate your help by getting us know about your user review. Also, web links to software and DLL vendors are provided just for your conform, and we cannot guarantee its accuracy nor relevance with DLL or process listed on this page. We are not affiliated with this pages. We are not responsible for misprints on this site or changes occured since this page was published. The product, software and operating system names mentioned on this web site, can be copyrighted and registered trademarks of their owners.